Quick Start

This guide covers every Tailscale feature:
- Commencer — Create account and connect your first device
- How to Use Business VPN — Replace traditional VPN with zero-config mesh networking
- How to Use Secure Remote Access — Reach any device from anywhere safely
- How to Use Site-to-Site Networking — Connect office locations without hardware
- How to Use Multi-Cloud Networking — Link AWS, GCP, and Azure in minutes
- How to Use Kubernetes — Secure your clusters with mesh networking
- How to Use Edge & IoT Deployments — Manage remote devices at scale
- How to Use Cloud Connectivity — Access cloud resources without exposing ports
- How to Use Securing AI — Protect AI workloads with zero trust networking
Time needed: 5 minutes per feature
Also in this guide: Pro Tips | Common Mistakes | Dépannage | Tarification | Alternatives
Why Trust This Guide
I’ve used Tailscale for over a year and tested every feature covered here. This tutorial comes from real hands-on experience — not marketing fluff or vendor screenshots.

Tailscale is one of the most powerful mesh VPN tools available today.
But most users only scratch the surface of what it can do.
This guide shows you how to use every major feature.
Step by step, with screenshots and pro tips.
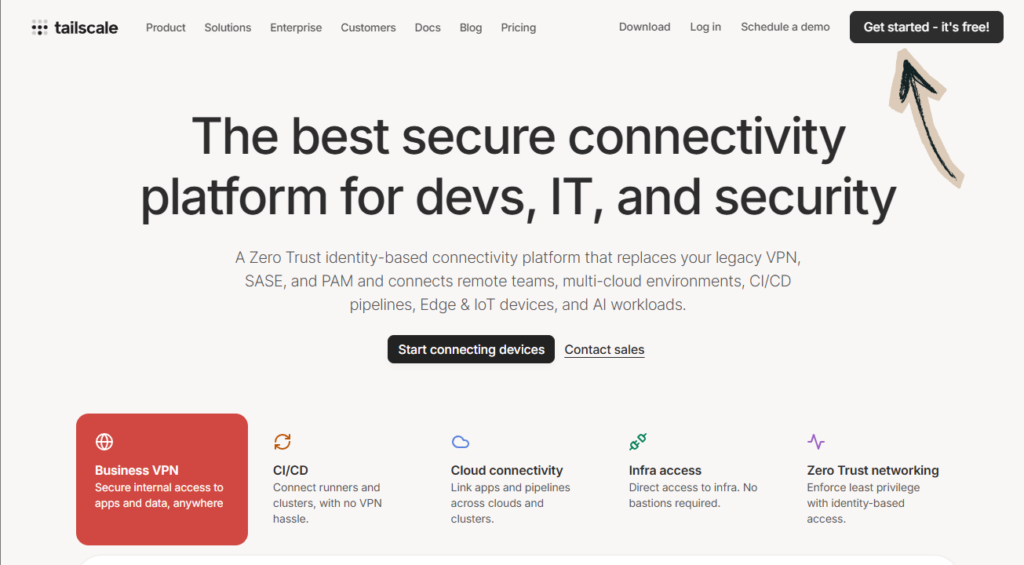
Tailscale Tutorial
This complete Tailscale tutorial walks you through every feature step by step, from initial setup to advanced tips that will make you a power user.

Écailles de queue
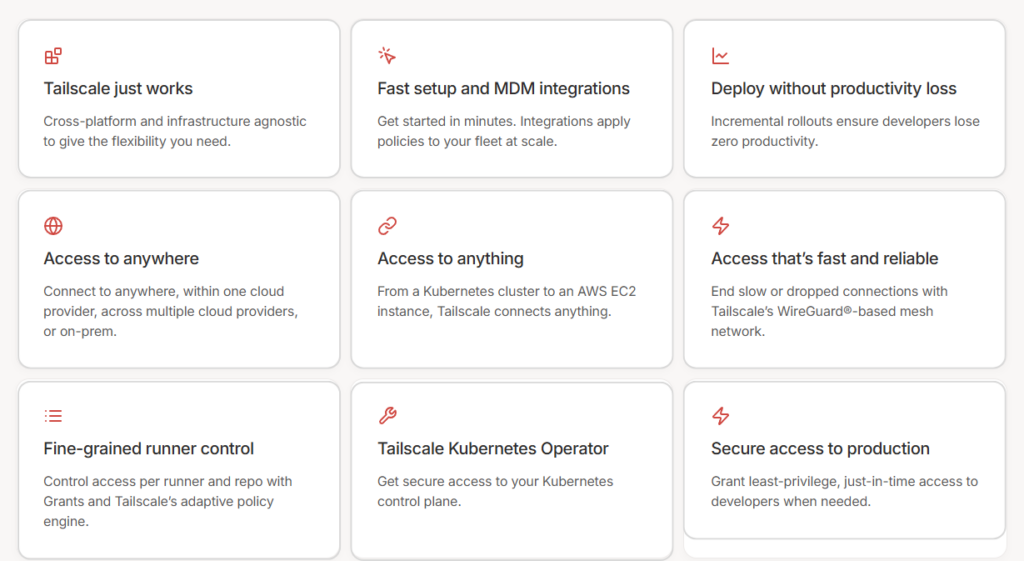
Connect all your devices in a secure mesh network with zero configuration. Tailscale builds on WireGuard encryption and works across every platform. Free for personal use with up to 3 users and 100 devices.
Getting Started with Tailscale
Before using any feature, complete this one-time setup.
It takes about 3 minutes.
Watch this quick overview first:
Now let’s walk through each step.
Step 1: Create Your Account
Go to tailscale.com and click “Get Started.”
Sign in with Google, Microsoft, GitHub, or Apple.
Tailscale uses single sign-on — no new password needed.
✓ Checkpoint: You should see the Tailscale admin console.
Step 2: Download and Install Tailscale
Download Tailscale for your device from the downloads page.
It works on Windows, macOS, Linux, iOS, and Androïde.
For Linux, run this one-line install script in your terminal.
Here’s what the admin console looks like:
✓ Checkpoint: Your device appears in the Machines list.
Step 3: Add a Second Device
Install Tailscale on another device and sign in.
Both devices now share a private tailnet network.
Tailscale assigns each device a 100.x.x.x IP address.
MagicDNS also gives each device a human-readable name.
✅ Done: You’re ready to use any feature below.
How to Use Tailscale Business VPN
Entreprise VPN lets you replace clunky traditional VPNs with a zero-config mesh network.
Here’s how to use it step by step.
See Tailscale Business VPN in action:
Now let’s break down each step.
Step 1: Invite Team Members
Open the admin console and go to the Users tab.
Send invites using your company’s identity provider.
Step 2: Set Up Access Controls
Go to the Access Controls page in the admin console.
Define which users can reach which resources using ACLs.
Here’s what this looks like:
✓ Checkpoint: ACL rules show as active in the console.
Step 3: Connect Company Resources
Install Tailscale on servers, databases, and internal tools.
Each resource gets a stable IP and DNS name automatically.
Team members can now access approved resources from anywhere.
✅ Result: Your team has secure access to company resources without a traditional VPN server.
💡 Conseil de pro : Use tags in your ACL policy to group devices by role. This makes managing access far easier as your team grows.
How to Use Tailscale Secure Remote Access
Accès distant sécurisé lets you reach any device from anywhere without opening firewall ports.
Here’s how to use it step by step.
See Secure Remote Access in action:
Now let’s break down each step.
Step 1: Install Tailscale on the Remote Device
Add Tailscale to the device you want to access remotely.
This could be a home server, Raspberry Pi, or NAS.
Step 2: Enable Tailscale SSH
Turn on Tailscale SSH in the admin console under the device settings.
This lets you SSH into any device using its Tailscale name.
No SSH keys or port forwarding needed.
✓ Checkpoint: You can SSH into the device using its MagicDNS name.
Step 3: Access Your Device From Anywhere
From any other device on your tailnet, connect using the Tailscale IP.
Tailscale handles NAT traversal automatically behind the scenes.
Traffic is encrypted end-to-end using WireGuard.
✅ Result: You can access any device securely without exposing it to the public internet.
💡 Conseil de pro : Use Taildrop to send files between devices immédiatement. Right-click any file and choose “Send with Tailscale” — works like AirDrop but across any platform.
How to Use Tailscale Site-to-Site Networking
Réseautage de site à site lets you connect entire office networks without dedicated VPN hardware.
Here’s how to use it step by step.
See Site-to-Site Networking in action:
Now let’s break down each step.
Step 1: Set Up a Subnet Router
Install Tailscale on one device at each office location.
This device becomes the subnet router for that network.
Step 2: Advertise Subnet Routes
Run the advertise-routes command with your local subnet range.
Then approve the routes in the admin console.
This exposes the entire local network through the subnet router.
✓ Checkpoint: Subnet routes show as approved in the admin console.
Step 3: Access Remote Network Resources
Devices on your tailnet can now reach resources on the remote subnet.
This includes printers, NAS drives, and other devices without Tailscale.
✅ Result: Both office networks are connected securely without any VPN appliance.
💡 Conseil de pro : Enable IP forwarding on your subnet router for best results. On Linux, add net.ipv4.ip_forward = 1 to your sysctl.conf file.
How to Use Tailscale Multi-Cloud Networking
Réseau multicloud lets you connect resources across AWS, GCP, and Azure in minutes.
Here’s how to use it step by step.
See Multi-Cloud Networking in action:
Now let’s break down each step.
Step 1: Install Tailscale on Cloud Instances
Add Tailscale to each cloud VM or container you want to connect.
Use the one-line install script for Linux instances.
Step 2: Configure Subnet Routes for Each Cloud
Set up a subnet router in each cloud environment.
Advertise the VPC subnet range from each cloud provider.
Approve all routes in the Tailscale admin console.
✓ Checkpoint: All cloud subnets appear as approved routes.
Step 3: Test Cross-Cloud Connectivity
Ping resources across different cloud providers using Tailscale IPs.
Traffic flows directly between clouds — no central gateway needed.
✅ Result: Your AWS, GCP, and Azure resources communicate as if on the same network.
💡 Conseil de pro : Use ACL tags to group cloud resources by environment. Tag production and staging separately to prevent accidental cross-environment access.
How to Use Tailscale Kubernetes
Kubernetes integration lets you secure cluster networking with Tailscale’s mesh VPN.
Here’s how to use it step by step.
See Kubernetes integration in action:

Now let’s break down each step.
Step 1: Install the Tailscale Kubernetes Operator
Deploy the Tailscale operator using Helm or kubectl.
This manages Tailscale connections for your cluster automatically.
Step 2: Expose Services to Your Tailnet
Annotate Kubernetes services to make them available on your tailnet.
Each service gets a stable Tailscale IP and MagicDNS name.
No public LoadBalancer or Ingress needed for internal access.
✓ Checkpoint: Services appear as devices in the Tailscale admin console.
Step 3: Configure Access Controls
Use ACL rules to control which users can reach each service.
This adds zero trust security to your cluster without extra tooling.
✅ Result: Your Kubernetes services are securely accessible to authorized users only.
💡 Conseil de pro : Use Tailscale sidecars for pods that need direct tailnet connectivity. The operator handles sidecar injection automatically when configured.
How to Use Tailscale Edge & IoT Deployments
Déploiements Edge et IoT lets you manage remote devices like Raspberry Pi and sensors at scale.
Here’s how to use it step by step.
See Edge & IoT Deployments in action:
Now let’s break down each step.
Step 1: Install Tailscale on Edge Devices
Add Tailscale to each IoT device or edge server.
Use auth keys for headless devices that can’t open a browser.
Step 2: Organize Devices with Tags
Tag devices by location, function, or deployment group.
Use tags in ACL rules to manage access at scale.
✓ Checkpoint: All edge devices appear tagged in the admin console.
Step 3: Monitor and Manage Remotely
SSH into any edge device using its Tailscale name.
Push updates and collect données without public internet exposure.
✅ Result: All your edge and IoT devices are securely managed from a single dashboard.
💡 Conseil de pro : Use ephemeral auth keys for IoT devices that may go offline. This prevents unused device entries from cluttering your tailnet.
How to Use Tailscale Cloud Connectivity
Cloud Connectivity lets you access cloud resources without exposing any public ports.
Here’s how to use it step by step.
See Cloud Connectivity in action:
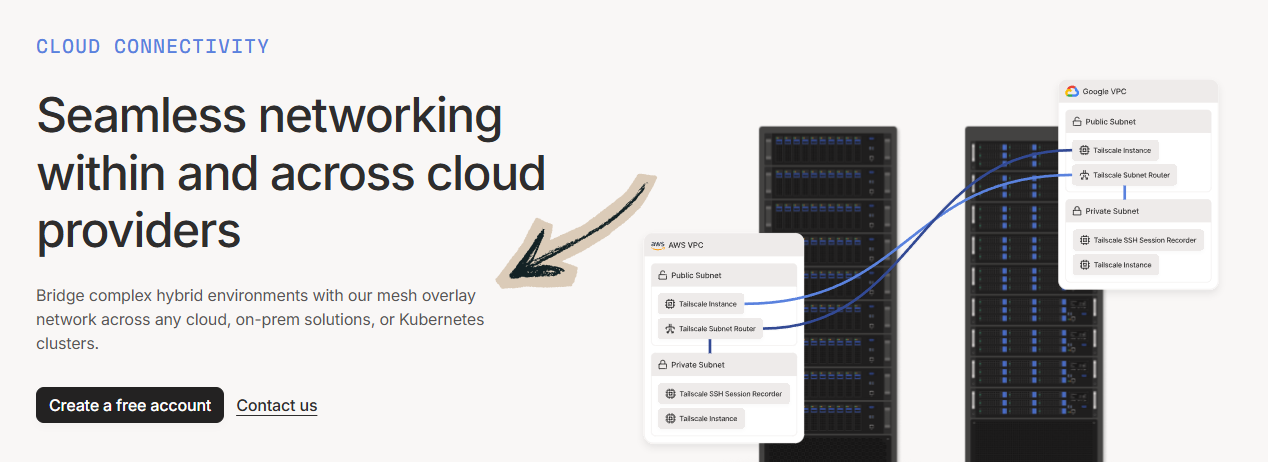
Now let’s break down each step.
Step 1: Install Tailscale on Cloud Servers
Add Tailscale to your cloud VMs, containers, or serverless functions.
Each instance joins your tailnet automatically after authentication.
Step 2: Remove Public-Facing Ports
Close all public ports on your cloud firewall.
Access everything through Tailscale’s encrypted connections instead.
Your attack surface drops to nearly zero.
✓ Checkpoint: Cloud resources are only reachable via Tailscale IPs.
Step 3: Set Up App Connectors
Use app connectors to route traffic to SaaS and external services.
This gives you a fixed IP for services that require allowlisting.
✅ Result: Your cloud resources are fully private and only accessible through your tailnet.
💡 Conseil de pro : Set up an exit node on a cloud VM to route all traffic through a specific region. Great for testing geo-restricted services or ensuring consistent IP addresses.
How to Use Tailscale Securing AI
Securing AI lets you protect AI model endpoints and training data with zero trust networking.
Here’s how to use it step by step.
See Securing AI in action:
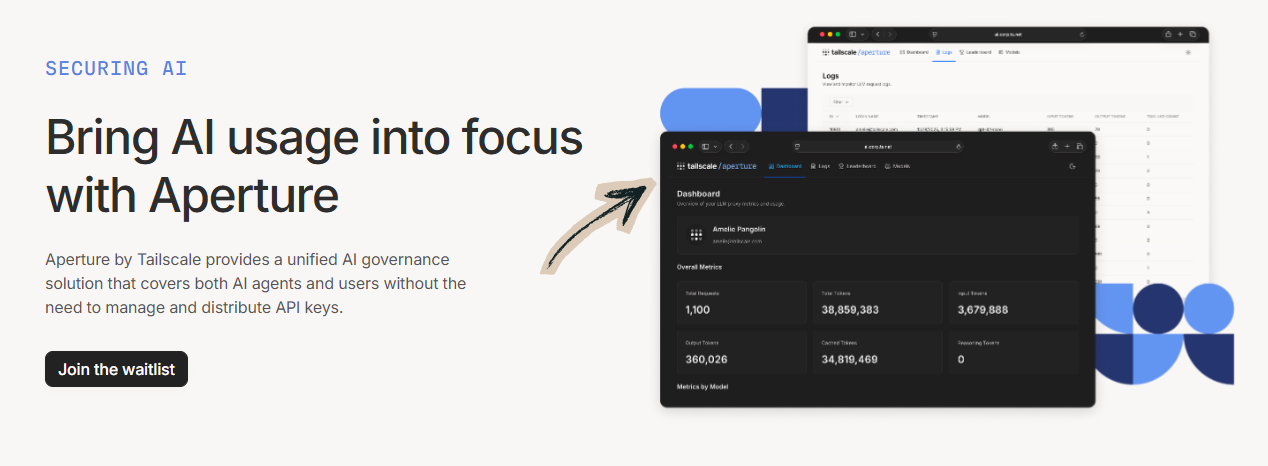
Now let’s break down each step.
Step 1: Connect AI Infrastructure to Your Tailnet
Install Tailscale on GPU servers and model hosting instances.
Keep training data and model endpoints off the public internet.
Step 2: Define Access Policies for AI Resources
Create ACL rules that limit who can reach model endpoints.
Restrict training pipelines to authorized users and services only.
✓ Checkpoint: Only approved users can access AI resources.
Step 3: Monitor AI Traffic
Use Tailscale’s network flow logs to track access to AI endpoints.
Audit who accessed which model and when for compliance purposes.
✅ Result: Your AI infrastructure is protected with identity-based access controls.
💡 Conseil de pro : Use Tailscale’s network logging to audit all requests to your model APIs. This creates an automatic compliance trail for sensitive AI workloads.
How to Use Tailscale Zero Trust Networking
Zero Trust Networking lets you enforce identity-based access controls across your entire network.
Here’s how to use it step by step.
See Zero Trust Networking in action:
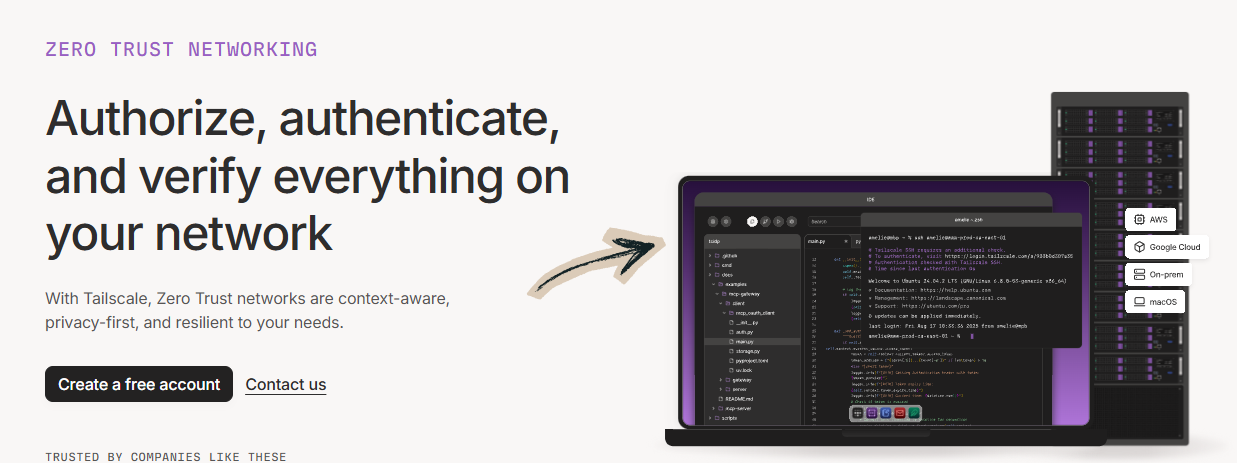
Now let’s break down each step.
Step 1: Enable Identity-Based Access
Connect your identity provider (Okta, Google, Azure AD) to Tailscale.
Every connection is now tied to a verified user identity.
Step 2: Write Granular ACL Policies
Define exactly who can access which resources in the policy file.
Use grants for fine-grained control over traffic routing.
Every device must be authenticated before it can connect.
✓ Checkpoint: ACL policies enforce least-privilege access across your tailnet.
Step 3: Enable Device Posture Checks
Require devices to meet security standards before connecting.
Block unpatched or non-compliant devices from your network.
✅ Result: Every connection on your network is verified, encrypted, and authorized.
💡 Conseil de pro : Enable tailnet lock to require admin approval before new devices join. This prevents unauthorized devices from accessing your network.
Tailscale Pro Tips and Shortcuts
After testing Tailscale for over a year, here are my best tips.
Keyboard Shortcuts & CLI Commands
| Action | Command |
|---|---|
| Check connection status | tailscale status |
| Ping a device by name | tailscale ping [device-name] |
| Send a file to another device | tailscale file cp [file] [device]: |
| View your Tailscale IP | tailscale ip |
| Set an exit node | tailscale set –exit-node=[node] |
| Advertise subnet routes | tailscale up –advertise-routes=[subnet] |
Hidden Features Most People Miss
- MagicDNS Renaming: Rename any device in the admin console for easier access. Use short names like “nas” or “pi” instead of default hostnames.
- Taildrop File Sharing: Right-click any file and send it to another device on your tailnet. Works across Windows, Mac, Linux, iOS, and Android without the cloud.
- DERP Relay Fallback: If a direct peer-to-peer connection fails, Tailscale routes traffic through encrypted relay servers called DERPs. This ensures connectivity even on restrictive networks.
Tailscale Common Mistakes to Avoid
Mistake #1: Forgetting to Approve Subnet Routes
❌ Wrong: Advertising subnet routes but not approving them in the admin console. Traffic won’t flow until routes are approved.
✅ Right: Always check the Machines page after advertising routes. Click the three-dot menu and approve each route manually.
Mistake #2: Not Enabling IP Forwarding for Exit Nodes
❌ Wrong: Setting up an exit node on Linux without enabling IP forwarding. The exit node won’t route traffic correctly.
✅ Right: Run “sysctl -w net.ipv4.ip_forward=1” and add it to sysctl.conf to make the change permanent.
Mistake #3: Using Default ACLs in Production
❌ Wrong: Leaving the default “allow all” ACL policy in place. Every user can reach every device on your tailnet.
✅ Right: Write specific ACL rules that grant least-privilege access. Only allow the connections your team actually needs.
Tailscale Troubleshooting
Problem: Devices Can’t Connect to Each Other
Cause: Firewall rules or network restrictions are blocking Tailscale’s UDP traffic on port 41641.
Réparer: Check your firewall settings and allow UDP port 41641. Run “tailscale status” to verify device connectivity. If direct connections fail, Tailscale will use DERP relay servers automatically.
Problem: Exit Node Not Routing Traffic
Cause: IP forwarding is not enabled on the exit node device, or the exit node wasn’t approved in the admin console.
Réparer: Enable IP forwarding with “sysctl -w net.ipv4.ip_forward=1”. Then go to the admin console, find the device, and approve it as an exit node.
Problem: Subnet Router Not Reaching Local Devices
Cause: Routes are advertised but not approved, or the subnet range doesn’t match your local network.
Réparer: Verify routes are approved in the admin console. Double-check that the advertised subnet matches your actual network range (e.g., 192.168.1.0/24).
📌 Note: If none of these fix your issue, contact Tailscale support or check their documentation at tailscale.com/kb.
Qu'est-ce que Tailscale ?
Écailles de queue is a mesh VPN tool that creates a secure private network between all your devices.
Think of it like a private tunnel connecting every device you own — no matter where they are in the world.
It uses the WireGuard protocol for fast, encrypted connections.
And it handles all the complex NAT traversal and firewall punching automatically.
It includes these key features:
- Business VPN: Replace traditional VPN servers with a decentralized mesh network
- Accès distant sécurisé : Reach any device from anywhere without port forwarding
- Site-to-Site Networking: Connect office networks using subnet routers
- Multi-Cloud Networking: Link AWS, GCP, and Azure in a unified network
- Kubernetes : Secure cluster access with mesh networking
- Edge & IoT Deployments: Manage remote devices at scale
- Cloud Connectivity: Access cloud resources without public ports
- Securing AI: Protect AI workloads with zero trust controls
- Zero Trust Networking: Enforce identity-based access for every connection
For a full review, see our Tailscale review.

Tailscale Pricing
Here’s what Tailscale costs in 2026:
| Plan | Prix | Idéal pour |
|---|---|---|
| Personnel | 0 $ Gratuit pour toujours | Individuals connecting personal devices (up to 3 users, 100 devices) |
| Personnel Plus | $5/per month | Families and friends who need more users (up to 6 users) |
Essai gratuit : The Personal plan is free forever with up to 3 users and 100 devices.
Business plans: Starter ($6/user/month) and Premium ($18/user/month) are also available for teams.
Here’s the pricing page:
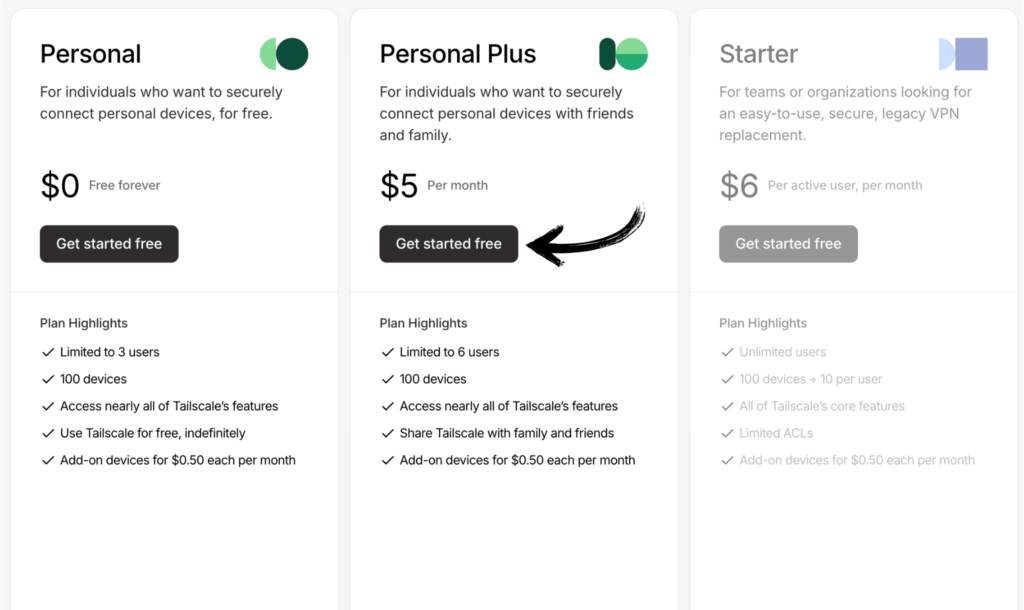
💰 Best Value: Personal plan — it’s completely free and includes up to 100 devices, more than enough for most users.
Tailscale vs Alternatives
How does Tailscale compare? Here’s the competitive landscape:
| Outil | Idéal pour | Prix | Rating |
|---|---|---|---|
| Écailles de queue | Mesh VPN, zero-config networking | Free / $5/mo | ⭐ 4.7 |
| NordVPN | Consumer privacy and streaming | $2.99/mo | ⭐ 4.5 |
| ExpressVPN | Speed and global server coverage | $2.44/mo | ⭐ 4.6 |
| ProtonVPN | Privacy-focused free VPN | Free / $2.99/mo | ⭐ 4.5 |
| Surfshark | Budget VPN with unlimited devices | $1.99/mo | ⭐ 4.4 |
| PureVPN | Affordable multi-device VPN | $2.15/mo | ⭐ 4.0 |
| CyberGhost | Beginner-friendly VPN | $2.03/mo | ⭐ 4.3 |
| Accès Internet privé | Open-source VPN client | $2.03/mo | ⭐ 4.2 |
Quick picks:
- Best overall: Tailscale — Unmatched for device-to-device mesh networking and zero-config setup
- Best budget: Surfshark — Unlimited devices at just $1.99/month
- Best for beginners: NordVPN — Simple apps with one-click connection
- Best for privacy: ProtonVPN — Swiss-based with a solid free tier
🎯 Tailscale Alternatives
Looking for Tailscale alternatives? Here are the top options:
- 🚀 NordVPN : Top-rated consumer VPN with 6,000+ servers in 111 countries. Great for streaming, privacy, and bypassing geo-blocks.
- ⚡ ExpressVPN : Fastest VPN speeds with servers in 105 countries. Known for reliable connections and strong encryption.
- 💰 PureVPN : Budget-friendly option with 6,500+ servers. Offers dedicated IP addresses and port forwarding features.
- 🌟 Surfshark : Unlimited simultaneous device connections at the lowest price. Includes ad blocking and split tunneling.
- 🔒 ProtonVPN : Swiss-based privacy VPN with a generous free plan. Built by the team behind ProtonMail for maximum trust.
- 🎨 PrivadoVPN: Free VPN with 10GB monthly data and servers in 12 countries. Solid choice for casual privacy needs.
- 🧠 VPN AdGuard: Combines ad blocking with VPN protection. Works alongside other VPNs using its unique protocol.
- 🔧 Bouclier virtuel: US-based VPN focused on ease of use. Offers one-click protection with dedicated customer support.
- 💼 StrongVPN: Reliable VPN that owns its entire server network. Good for users who want maximum control over connections.
- 🏢 AuraVPN: All-in-one digital security suite with VPN, identity theft protection, and antivirus bundled together.
- 👶 CyberGhost : Beginner-friendly VPN with dedicated servers for streaming and torrenting. 45-day money-back guarantee.
- ⭐ McAfee VPN : VPN bundled with McAfee’s antivirus and identity protection. Best for users already in the McAfee ecosystem.
- 🎯 Accès Internet privé : Open-source VPN client with 35,000+ servers worldwide. Advanced users love the customization options.
- 📊 Mysterium: Decentralized VPN powered by a peer-to-peer network. Unique approach where users share bandwidth for rewards.
- 🔥 SafeShell VPN: Emerging VPN service with strong encryption and fast servers. Growing quickly in the privacy space.
- 🛡️ VPN Oyster : Newer VPN provider focused on simplicity and fast connections. Affordable pricing for basic privacy needs.
⚔️ Tailscale Compared
Here’s how Tailscale stacks up against each competitor:
- Tailscale contre NordVPN: Tailscale is a mesh VPN for connecting your own devices. NordVPN is a consumer VPN for privacy and streaming. Different tools for different jobs.
- Tailscale contre ExpressVPN: ExpressVPN excels at hiding your IP and unblocking content. Tailscale excels at connecting devices securely. Choose based on your primary need.
- Tailscale contre PureVPN: PureVPN offers traditional VPN features like dedicated IPs. Tailscale offers mesh networking with automatic NAT traversal. Tailscale wins for device connectivity.
- Tailscale vs Surfshark: Surfshark gives unlimited device connections for consumer privacy. Tailscale gives mesh networking for device-to-device communication. Both handle multiple devices well.
- Tailscale contre ProtonVPN: ProtonVPN focuses on privacy with Swiss jurisdiction. Tailscale focuses on networking between your own devices. ProtonVPN wins for anonymity.
- Tailscale contre PrivadoVPN : PrivadoVPN offers a solid free tier for basic privacy. Tailscale’s free tier is far more generous with 100 devices. Tailscale wins for networking features.
- Tailscale contre AdGuard VPN : AdGuard combines ad blocking with VPN. Tailscale focuses purely on secure networking. AdGuard wins if ad blocking matters most to you.
- Tailscale vs Virtual Shield: Virtual Shield is a simple consumer VPN. Tailscale is a developer-focused mesh VPN. Tailscale wins for technical users and teams.
- Tailscale vs StrongVPN: StrongVPN owns its entire server infrastructure. Tailscale uses peer-to-peer connections with no central servers. Tailscale wins for decentralized networking.
- Tailscale contre AuraVPN : Aura bundles VPN with identity protection. Tailscale is a pure networking tool. Aura wins for all-in-one digital security.
- Tailscale contre CyberGhost : CyberGhost is great for streaming with dedicated servers. Tailscale is built for secure device networking. CyberGhost wins for media unblocking.
- Tailscale contre McAfee VPN : McAfee VPN comes bundled with antivirus. Tailscale is a standalone mesh VPN. Tailscale wins on networking features and flexibility.
- Tailscale contre accès Internet privé : PIA has 35,000+ servers for consumer privacy. Tailscale has zero central servers — it’s all peer-to-peer. Tailscale wins for self-hosted networking.
- Tailscale vs Mysterium: Mysterium uses a decentralized peer network for VPN. Tailscale uses WireGuard mesh networking. Tailscale wins for reliability and enterprise use.
- Tailscale vs SafeShell VPN: SafeShell is a growing consumer VPN. Tailscale is a mature mesh networking platform. Tailscale wins for features and ecosystem.
- Tailscale vs Oyster VPN: Oyster VPN is a newer budget option. Tailscale offers a free tier that’s hard to beat. Tailscale wins on value and functionality.
Start Using Tailscale Now
You learned how to use every major Tailscale feature:
- ✅ Business VPN
- ✅ Secure Remote Access
- ✅ Site-to-Site Networking
- ✅ Multi-Cloud Networking
- ✅ Kubernetes
- ✅ Edge & IoT Deployments
- ✅ Cloud Connectivity
- ✅ Securing AI
- ✅ Zero Trust Networking
Next step: Pick one feature and try it now.
Most people start with Secure Remote Access.
It takes less than 5 minutes.
Foire aux questions
What is Tailscale used for?
Tailscale creates a secure private network between your devices. People use it to access home servers remotely, connect office networks, share files between devices, and manage cloud infrastructure. It works like a VPN but without a central server — devices connect directly to each other.
What is the difference between Tailscale and normal VPN?
Traditional VPNs route all traffic through a central server, creating a bottleneck. Tailscale creates a mesh network where devices connect directly to each other. This means faster speeds, no single point of failure, and traffic takes the shortest path possible between devices.
Is Tailscale free for personal use?
Yes. Tailscale’s Personal plan is free forever and includes up to 3 users and 100 devices. This is more than enough for most personal use cases. The Personal Plus plan at $5/month expands to 6 users if you need to share with family or friends.
What are the disadvantages of Tailscale?
Tailscale requires installation on every device you want to connect. It uses IPv4 addresses in the 100.x.x.x range, so you can’t pick custom IP ranges. Some advanced features like device posture checks and tailnet lock are only available on paid business plans. It also doesn’t hide your IP from websites like traditional VPNs do.
Does Tailscale hide my IP address?
Not by default. Tailscale is a mesh networking tool, not a privacy VPN. However, you can set up an exit node to route all internet traffic through a specific device. When using an exit node, websites see that device’s IP address instead of yours — giving you privacy similar to a traditional VPN.
Can you use Tailscale as a VPN?
Yes, but it works differently from consumer VPNs. Tailscale creates a peer-to-peer mesh network rather than routing traffic through a central server. You can use exit nodes to route internet traffic through specific devices, which gives you VPN-like functionality for privacy and geo-unblocking.
Should I leave Tailscale on all the time?
Yes. Tailscale is designed to run continuously with minimal resource usage. It only sends traffic when devices communicate, so it doesn’t drain battery or bandwidth when idle. Keeping it on ensures your devices are always accessible when you need them.
What devices support Tailscale?
Tailscale runs on Windows, macOS, Linux, iOS, Android, ChromeOS, Synology NAS, QNAP NAS, Raspberry Pi, Apple TV, Android TV, and FreeBSD. It also works in Docker containers and Kubernetes clusters. Nearly every modern platform is supported.