
Feeling overwhelmed by online security?
It’s tough to keep your important systems safe when so many people need access.
That’s where BeyondTrust comes in.
Our quick guide will show you how to use BeyondTrust.
Let’s get started and make your systems safer!

Seeking unmatched security and precise control for your enterprise? Try now!
Getting Started with BeyondTrust
Understanding the Basics
So, what exactly is BeyondTrust?
Think of it like a very smart security guard for your computer systems.
It helps you control who can access your most important stuff, like servers or special programs.
This is called “Privileged Access Management,” or PAM for short.
BeyondTrust helps you give people just enough access to do their jobs, and no more.
This makes your whole system much safer.
Setting Up Your Account
Ready to start?
First, you’ll need to get into BeyondTrust.
This means either signing up for a new account or logging into one you already have.
It’s like creating an account for any online service.
You’ll put in some basic information, like your name and email.
Make sure you have details ready for the main person who will be in charge, like an administrator.
Getting this part right sets you up for smooth sailing.
Navigating the Interface
Once you’re logged in, you’ll see the BeyondTrust main screen.
This is your dashboard.
Don’t worry, it’s not super complicated!
Spend a few minutes clicking around.
You’ll quickly get a feel for where everything is and how to find what you need.
It’s designed to be simple to use.

Managing Users and Permissions
Adding Users to BeyondTrust
Now that you’re in, let’s add the people who will be using your systems.
Think of it like making a guest list for your house, but for your computers.
BeyondTrust makes it easy to add new users, one by one.
You’ll put in their names and a few other details.
There might be different types of users, like someone who can manage everything or someone who just needs to see reports.
Assigning Roles and Permissions
After you add a user, you need to tell BeyondTrust what they are allowed to do.
This is where “roles” and “permissions” come in.
A “role” is like a job title that comes with a set of rules.
For example, a “server manager” role might let someone access all your servers.
You simply pick the right role for each user.
This is a smart way to keep things safe.

Creating Groups for Easier Management
Imagine you have a whole team of people who all need the exact same access to certain systems.
Instead of setting up each person one by one, you can put them into a “group.
” It’s like putting all the ‘sales team’ members into one group.
Then, you just give that whole group the right permissions.
This saves a lot of time and keeps things neat!
Securing Your Assets
Defining “Assets” in BeyondTrust
What are “assets” in BeyondTrust?
Think of them as all the valuable things you need to protect.
These aren’t just cash or jewels. In the computer world, assets are your important systems, like:
- Servers: These are big computers that store information and run programs for your whole business.
- Databases: These are like huge digital filing cabinets where all your important data lives.
- Network devices: These are things like routers and switches that help your computers talk to each other.
- Special programs: Any software that holds important information or lets you do critical tasks.
Listing all your assets in BeyondTrust is the first step to ensuring their safety.
It’s like taking inventory of everything valuable in your home.
Adding Assets to BeyondTrust
Now that you know what your assets are, let’s add them to BeyondTrust.
It’s a straightforward process.
You’ll go to a section where you can list each one.
You might also add notes about why it’s important.
Granting Access to Assets
Once your assets are listed, you need to tell BeyondTrust who can use them and how.
This is where you connect your users or groups to the specific assets they need to work with.
For example, you can say, ” The IT Support group can access the Main Web Server from 9 AM to 5 PM.
BeyondTrust lets you be very exact.
And if someone no longer needs access to an asset, you can easily remove it.
This keeps your systems locked down and only accessible to the right people at the right time.
Monitoring and Reporting
Tracking User Activity
After setting up who can access what, you’ll want to keep an eye on things.
Because it’s super important for security and for showing that you’re following the rules.
BeyondTrust helps you see exactly what users are doing.
It’s like having a security camera that records every login, every file opened, and every action taken.
This way, if something looks off, you’ll know right away.
Generating Reports
BeyondTrust can also create helpful summaries of all this activity.
These are called “reports.” You can ask it to show you things like:
- Who logged in the most today?
- Were there any failed login attempts?
- Which systems were accessed by a certain person?
These reports are like easy-to-read printouts that give you a clear picture of what’s going on.
They are great for checking if everything is secure and for showing auditors that you are keeping good tabs on your systems.
You can create simple reports quickly, giving you the information you need at a glance.
Setting Up Alerts
Imagine your security guard could instantly tap you on the shoulder if something unusual happened.
That’s what alerts do in BeyondTrust!
Getting these notifications quickly means you can act fast if there’s a problem.
It’s like having an early warning system that keeps you one step ahead of potential issues.
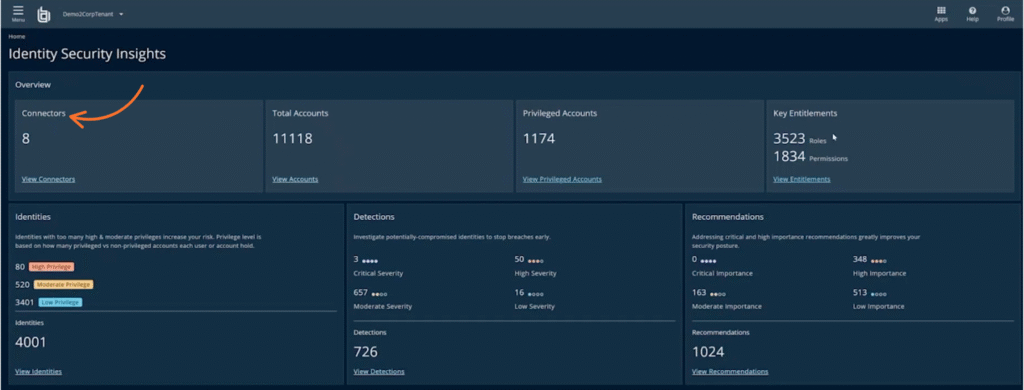
Conclusion
We’ve covered how to use BeyondTrust.
We looked at setting it up.
We learned about adding users and giving them the right permissions.
We also talked about securing your important computer assets.
And we saw how to watch what’s happening and get reports.
BeyondTrust helps make your online world safer.
It lets you control who sees your private information.
This stops bad things from happening.
It also makes your job easier by keeping things neat.
Protecting special access is really important now.
BeyondTrust gives you a strong tool for this.
Alternatives to BeyondTrust
Here’s how BeyondTrust stacks up against some alternatives, focusing on their standout features:
- Getscreen: Offers quick, browser-based access for easy remote support, very user-friendly.
- TeamViewer: Known for wide cross-platform compatibility and robust all-around remote connectivity.
- AnyDesk: Provides incredibly fast connections and a very lightweight application for quick access.
- Splashtop: Excels with high-quality streaming and a simple, user-friendly interface for remote work.
- RemotePC: Features always-on remote access and strong multi-monitor support for easy use.
- VNC Connect: Simple direct connections for screen sharing, prioritizing ease of use and compatibility.
- GoTo Resolve: Combines remote support with IT ticketing and asset management for unified control.
- ISL Online: Offers flexible self-hosting options and strong security for private cloud deployments.
- RealVNC Connect: Provides direct peer-to-peer connections with strong encryption for secure remote access.
- LogMeIn: Known for reliable remote access and straightforward file sharing, great for basic needs.
Frequently Asked Questions
What is privileged access management (PAM)?
PAM helps you control who has special access to your most important computer systems and data. It makes sure only the right people can use powerful credentials, like administrator passwords, to keep everything safe.
How does BeyondTrust protect remote access?
BeyondTrust secures remote desktop connections. It ensures that when someone connects to a desktop or server from far away, their access is controlled and monitored, even for RDP sessions.
Can BeyondTrust manage shared passwords?
Yes, BeyondTrust can store and manage shared passwords safely. It helps teams access accounts without knowing the actual credentials, making it much more secure and reducing risks.
Is BeyondTrust hard to set up for a small team?
No, BeyondTrust has a simple setup. Even for a small team, you can quickly get it running to manage access to your servers and remote desktop connections without a lot of hassle.
Does BeyondTrust record remote desktop sessions?
Yes, BeyondTrust can record remote desktop sessions. This means you can see exactly what happened during a desktop session, which is great for security checks and proving compliance.














