社内のすべてのノートパソコンと電話を管理するのは面倒ですか?
これらすべてのデバイスを追跡するのは大変な仕事です。
新たなオンラインの脅威からすべてを安全に保つことは困難です。
You feel like you are always chasing 安全 updates and lost equipment.
Intune の機能について詳しく説明します。
ここで Microsoft Intune が役立ちます。このツールは、デバイスのセキュリティと管理を簡素化することを約束します。

Microsoft Intune 2025のAIによる提案機能により、ポリシー設定時間を最大50%短縮し、時間を有効活用できます。もう問題追及に時間を費やす必要はありません。
Microsoft Intune とは何ですか?
Microsoft Intune is a cloud-based service.
Think of it as your single control center for all the デバイス 仕事や個人で使うもの。
これには、会社所有か個人所有かを問わず、すべてのノートパソコンと携帯電話が含まれます。
Intuneは、 仕事 エンドポイント管理とセキュリティを備えています。
このサービスは、Microsoft Intune プランを通じて利用できます。
さらに、エンドポイント権限管理機能も備えており、より優れた制御を実現します。
Microsoft Intune を作成したのは誰ですか?
この製品を開発した会社は マイクロソフト.
このサービスは、2010 年に Windows Intune という名前で初めて開始されました。
Microsoft’s big idea was simple.
They wanted a way to manage and protect devices from the cloud, not just from the office.
人々が仕事にさまざまなモバイルデバイスを使用するようになったため、これはさらに重要になりました。
これは会社を維持するのに役立ちます データ 従業員が効率的に働けるようにしながら、安全性を確保します。
主なメリット
- 統一 エンドポイント管理 (UEM) Intune provides a single, unified platform, the Intune Admin Center, for managing devices and apps across your entire IT environment. It brings together PC management and mobile management into a unified endpoint management solution.
- 強力なセキュリティソリューションは、アプリ保護ポリシーやデバイスコンプライアンスルールなどのツールを使用して、セキュリティを強化し、企業データを保護します。Intune は、Microsoft Defender for Endpoint やその他の Microsoft セキュリティツールと緊密に連携します。
- 多数のデバイスとオペレーティングシステムをサポート。Windowsデバイス、Androidデバイスなどのデバイスを管理できます。 iOS 単一のコンソールから、デバイス、デスクトップコンピューターまで、あらゆるデバイスを操作できます。この幅広いサポートにより、多種多様なデバイスやデバイスを簡単に管理できます。
- 簡略化 App Management and Deployment: The Intunestream app delivers, tracks app usage, and manages updates. It handles app deployment and helps manage software on devices, which is great for remote workforces.
- Secure UserAccess. It manages user access to your organizational resources using powerful to, such as conditional access. This ensures that only safe and compliant devices can obtain リモートアクセス, helping you manage end-user access.
- 個人デバイス(BYOD)のより優れた管理 - このサービスは、モバイルアプリケーション管理を活用することで、BYOD(個人所有デバイス持ち込み)シナリオをサポートします。これにより、個人デバイスを完全に制御することなく、企業データを保護できます。
- Microsoft サービスとのシームレスな統合 Intune は、Microsoft 365、Microsoft Configuration Manager、そして Microsoft 環境内のその他の Microsoft サービスとシームレスに統合されます。これにより、包括的な管理およびセキュリティ ソリューションが提供されます。

ベストフィーチャー
Microsoft Intune には、セキュリティとデバイスの管理方法を変える重要な機能が満載されています。
これらのユニークなツールは連携して動作するように構築されています。
これにより、エンドポイントをより効率的かつ迅速に管理できるようになります。
Here is a look at some of the best features for 2026.
1. コア機能
Intune では、高度な分析を使用して、デバイスの問題に先手を打つことができるようになりました。
デバイスの健全性、アプリのクラッシュ、起動時間に関するデータを収集します。
これは問題を見つけるのに役立ちます 前に 従業員もそれに気づくようになります。
これらの分析情報を活用して、仮想エンドポイントとユーザー エクスペリエンス全体を改善できます。
2. AIを活用したサイバーセキュリティ
これはセキュリティにとって画期的な出来事です。
Intune leverages AI-powered cybersecurity through its integration with Microsoft Security Copilot.
Accelerates threat analysis and recommends optimal security policies.
推測する必要がなくなり、問題への対応が速くなります。
3. エンドポイント管理
Intune は本質的に、エンドポイント管理の強力なツールです。
It provides a single console for setting up.
Securing and monitoring all your devices, from laptops to phones.
この集中管理は、すべてのデバイスが会社のガイドラインに準拠していることを確認するために不可欠です。
これが、この製品が Microsoft Endpoint Manager とも呼ばれる主な理由です。

4. クラウド向けディフェンダー
Intune は Defender for Cloud と連携して動作します。
この接続により、デバイスのセキュリティ ポリシーがクラウド セキュリティ ルールと一致するようになります。
It provides a more comprehensive.
Unified view of security across your entire digital landscape, protecting servers and cloud workloads.
5. エントラID
アクセス制御には、Entra ID (旧 Azure Active Directory) との緊密な統合が重要です。
Intune verifies identity and device security before granting access.
これが、強力なゼロ トラスト セキュリティ モデルを実施する方法です。
6. エントラインターネットアクセス
この機能は、Microsoft の Security Service Edge ソリューションの一部です。
Entra Internet Access は、安全な Web ゲートウェイとして機能します。
オフィス外でもインターネットの脅威やマルウェアからユーザーを保護します。
すべてのインターネット トラフィックにセキュリティ ポリシーを適用します。

7. セキュリティエクスポージャー管理
セキュリティ エクスポージャー管理は、環境全体で最も脆弱な場所を特定するのに役立ちます。
It collects data from all Microsoft security tools, including Intune.
To identify and prioritize your most significant security gaps.
最も重要な問題の解決に集中するのに役立ちます。
8. 攻撃対象領域の管理
Connected to exposure management.
Attack Surface Management works to reduce the ways an attacker can gain entry into your network.
忘れられたシステム、パッチが適用されていないソフトウェア、または誤って構成された設定を見つけるのに役立ちます。
攻撃対象領域を縮小することで、 作る あなたの組織にとって、より困難なターゲットとなります。
This is included with certain 仕事 premium plans.

9. DDoS攻撃対策
While Intune itself focuses on device and application security.
The entire Microsoft Security ecosystem, including Azure.
DDoS 保護 (分散型サービス拒否) を提供します。
これは、包括的なビジネス プレミアム プランに含まれていることがよくあります。

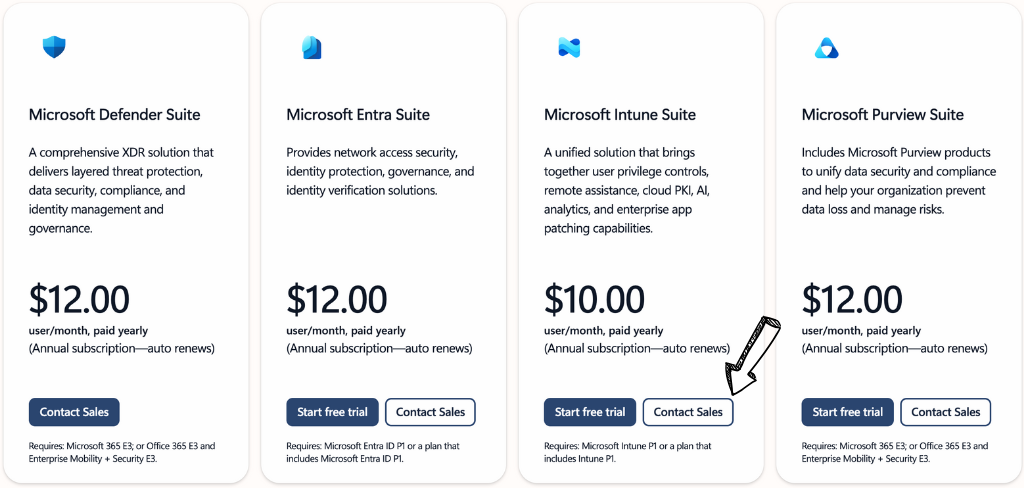
価格
| スイート名 | 価格(月額、年払い) | 必要な前提条件 |
| 必要条件: Microsoft 365 E3、または Office 365 E3 と Enterprise Mobility + Security E3。 | $12.00 | 必要条件: Microsoft 365 E3、または Office 365 E3 と Enterprise Mobility + Security E3。 |
| マイクロソフト エントラ スイート | $12.00 | 必要条件: Microsoft Entra ID P1 または Microsoft Entra ID P1 が含まれるプラン。 |
| Microsoft Intune スイート | $10.00 | 必要条件: Microsoft Intune P1 または Intune P1 が含まれるプラン。 |
| Microsoft Purview スイート | $12.00 | 必要条件: Microsoft 365 E3、または Office 365 E3 と Enterprise Mobility + Security E3。 |
長所と短所
Choosing the right tool means considering the entire picture.
Let us weigh the benefits and drawbacks of using Intune.
長所
短所
Microsoft Intune の代替
Microsoft Intune が最適ではないと判断した場合でも、多くの選択肢があります。
その他の強力な統合エンドポイント管理 (UEM) ツールは、異なる強みを提供します。
特に、会社が Microsoft 製品に大きく依存していない場合はそうです。
- アテラ: これはマネージドサービスプロバイダー(MSP)に人気のオールインワンプラットフォームです。RMM、ヘルプデスク、AIを活用した機能を組み合わせたものです。 オートメーションIT Autopilot や AI Copilot 機能などの IT チームの自律的な業務遂行を支援します。
- 忍者ワン: This is another highly-rated automated RMM and UEM platform known for its ease of use and strong customer support. It is a good choice for those who require simple yet powerful monitoring and パッチ管理.
- VMware Workspace ONE: このプラットフォームは、柔軟性の高いクロスプラットフォームUEMソリューションの提供に優れた主要な競合製品です。強力なゼロトラスト・セキュリティモデルと、Microsoftエコシステム外でも優れたサポートを提供することで知られています。
- ジャムプロ: 企業でAppleデバイス(Mac、iPad、iPhone)を主に使用している場合、Jamf Proは業界をリードする専門管理ツールです。Appleのオペレーティングシステムとの緊密な統合と最高の機能を提供します。
- ManageEngine エンドポイント セントラル: このソリューションは、包括的な機能セットと競争力のある価格で知られており、ユーザーフレンドリーなインターフェースを通じて強力なパッチ管理と資産管理機能を提供します。
- ブラックベリーUEM: これは、すべてのデバイスと通信に対して政府レベルのセキュリティと強力な暗号化を提供するため、規制の厳しい企業でよく選択されます。
個人的な経験
Our team came to Intune because we needed a single.
Reliable way to manage devices for our growing, remote staff.
Intune は、ついに制御と安全性を確保するためのツールを提供しました。
Intune がどのように優れた成果の達成に役立ったかをご紹介します。
- 合理化されたポリシー展開: ポリシー展開を利用して、セキュリティと設定のアップデートを自動的にプッシュ配信しました。50台のノートパソコンを1台ずつ修正する代わりに、Intuneで単一のポリシーを作成し、すべてのデバイスに均一に適用しました。
- 整理されたデバイスグループ: 営業やマーケティングなどの様々なチーム向けにカスタムデバイスグループを作成しました。 会計, which have distinct security requirements. This meant we could apply strict compliance policies to the 会計 team’s devices only.
- 強制的な高度なエンドポイント管理: Intuneの高度なエンドポイント管理機能を活用し、ディスク暗号化や強力なパスワードなどの機能が常に有効になっていることを確認しました。デバイスがこれらのルールを満たしていない場合は、フラグが付けられ、会社のファイルへのアクセスがブロックされました。
- 視認性の向上: ダッシュボードではデバイスの健全性を明確に把握できました。すべてのデバイスのコンプライアンス状況をリアルタイムで確認できたため、問題を迅速に解決することができました。
最終評決
Microsoft Intune は、デバイスを管理するための非常に強力な選択肢です。
すでに使用している Microsoft 365 環境に完全に統合されます。
Including securing remote workers and managing personal devices.
ビジネスが Microsoft 製品に大きく依存している場合。
Intune は、比類のない統合と集中管理を提供します。
これは、安全で効率的なデジタルワークプレイスへの強力な投資です。
よくある質問
What is Microsoft Intune used for?
It acts as a cloud-based command center for device management. Organizations use Intune to control how devices (laptops, phones) access corporate data, enforce security policies like password requirements, and deploy necessary applications remotely. It bridges the gap between security and productivity.
What can employers see with Microsoft Intune?
On a personal device (BYOD), visibility is limited. They can see device details like model, operating system version, and the list of managed business apps. They cannot see your personal photos, personal emails, 文章 messages, or file contents.
Can Microsoft Intune see browsing history?
Generally, no. Intune does not track your personal web surfing habits. However, if you are browsing through a managed corporate browser (like Edge for Business) or a company VPN profile, network traffic might be logged elsewhere, but Intune itself isn’t a browsing spy tool.
Is Microsoft Intune free or paid?
It is a paid service. Intune is typically included in Microsoft 365 subscriptions (like Business Premium or E3/E5) or the Enterprise Mobility + Security suites. There is no permanent free version, though 30-day trials are often available.
Is Microsoft Intune a MDM or MAM?
It is a powerhouse that handles both. It functions as Mobile Device Management (MDM) when you enroll and control the entire device. It also offers Mobile Application Management (MAM) to secure specific apps (like Outlook) without touching the rest of the phone.
What Microsoft licenses include Intune?
You get Intune with Microsoft 365 Business Premium, Microsoft 365 E3 and E5, and the Enterprise Mobility + Security (EMS) E3 and E5 plans. It allows businesses to bundle security costs rather than buying standalone tools.
What are the disadvantages of using Microsoft Intune?
Configuration can be complex. Because it offers granular control, setting it up correctly requires expertise. Additionally, users often resist installing it on personal phones due to privacy misconceptions, even though Intune’s visibility is restricted.
More Facts about Microsoft Intune
- Cost of extras: Microsoft Intune can get expensive because you often have to pay extra for special tools and advanced features.
- Non-Windows devices: Intune works with many devices, but it usually works best with Windows computers. It might not be as strong when used with Apple or アンドロイド デバイス。
- Support issues: Some users say that customer service for Intune has gotten worse and that the instruction manuals are sometimes old or out of date.
- All-in-one control: Intune is a “Unified Endpoint Management” (UEM) tool. This means it lets you control settings and updates for phones, tablets, and computers all from one place.
- Health checks: This software helps companies keep an eye on their devices to make sure they are working well and following company rules.
- Safety features: Intune uses strong security, like scrambling data (encryption) and blocking viruses, to keep information safe.
- Fighting viruses: It works together with Microsoft Defender to help companies stop hackers, find viruses, and fix security problems.
- Automatic scanning: Intune connects directly to Microsoft Defender to automatically scan files and tell the IT team if a device is in danger.
- Working with partners: Intune works with other popular services, like Google Play for apps and チームビューアー for fixing computers remotely.
- Web controls: There is a website for administrators to control Intune. Programmers can also use a tool called Microsoft Graph API to control it using code.
- Plan 2 extras: There is a paid upgrade called “Intune Plan 2.” It adds better security tools and detailed reports to the basic plan.
- The full suite: The “Intune Suite” is a bundle that includes everything from Plan 1 and Plan 2, plus even more advanced tools.
- Extra costs per person: Adding Intune Plan 2 costs about $4 extra for each user every month. The full Intune Suite costs about $10 extra per user.
- Buying it alone: You don’t always need a big bundle; companies can buy Intune Plan 1 all by itself.
- Free test: Companies can try out Intune for free to see if they like it before paying.
- Hidden costs: The price of using Intune can go up because many of the best features are not included in the base price and must be bought separately.
- Total package price: If a company doesn’t already own Microsoft licenses, getting everything set up with Intune can cost around $32 per user each month.
- Self-help app: Workers can use the “Company Portal” app or website to fix simple problems or download apps on their own.
- Work from anywhere: The people in charge (administrators) can manage company devices from anywhere as long as they have the internet.
- Advanced help: Intune has special features that let IT support staff take control of a screen to help fix it or manage special permissions.
- Price comparison: Many people think Microsoft Intune costs more than similar tools made by other companies.
- 業界リーダー: Experts who study technology rank Microsoft Intune as one of the best tools for managing devices.
- Pay-to-play features: Users have noticed that many important features require buying expensive “add-ons,” which makes the final bill higher.
- Confusing screens: The buttons and menus in Intune can be confusing. Some users feel overwhelmed because there are so many options to choose from.
- Tricky licenses: Figuring out how to pay for Intune can be hard. It is sometimes confusing to know if you are paying for each person or for each device.