Your company’s security is under constant attack.
Cyber threats are a huge problem, and it’s hard to keep up with each vulnerability.
Manually finding and fixing these issues is a time-consuming and labor-intensive process.
It’s a never-ending cycle of patching and praying.
But what if you didn’t have to do it all yourself?
What if there were a way to find and fix these weak spots automatically?
We’ll show you how a new approach called Autonom Vulnerability Management is changing the game and giving IT teams a powerful new tool.
The Old Way vs The New Way
Before, IT teams had to identify Sicherheit flaws manually.
Now, autonomous solutions like Atera’s IT Autopilot automatically handle the entire process, making your Geschäft more secure and efficient.
Manual Solutions
Have you ever wondered what IT was like before smart tools?
The old vulnerability management process was a lot of manual work.
Teams used to spend their days trying to keep up with every single threat.
They would run vulnerability scanners, get a long list of problems, and then have to figure out what was most important.
This manual approach to vulnerability management solutions often leads to delays and a higher chance of human error.
It was like trying to patch a leaky boat with a roll of tape—you might fix one hole, but a bunch of new ones pop up right behind it.
Think about it: an IT person gets a report of a dozen security vulnerabilities.
They have to decide which ones are the most dangerous.
This is often done through risk-based vulnerability management, where they figure out which critical vulnerabilities to tackle first.
It’s a smart way to work, but it still requires a lot of human thinking and action.
They had to install patches manually, hoping they wouldn’t break anything.
This created a slow, reactive cycle. You were always just a step behind the hackers.
Autonomous Solutions
That’s where Atera comes in. It’s a completely different way of doing things.
Instead of just giving you a list of identified vulnerabilities, Atera takes the next step.
It’s the ONLY real autonomous solution out there and the first to introduce this game-changing technology.
AI powers its vulnerability management program.
This means it can find and fix problems on its own.
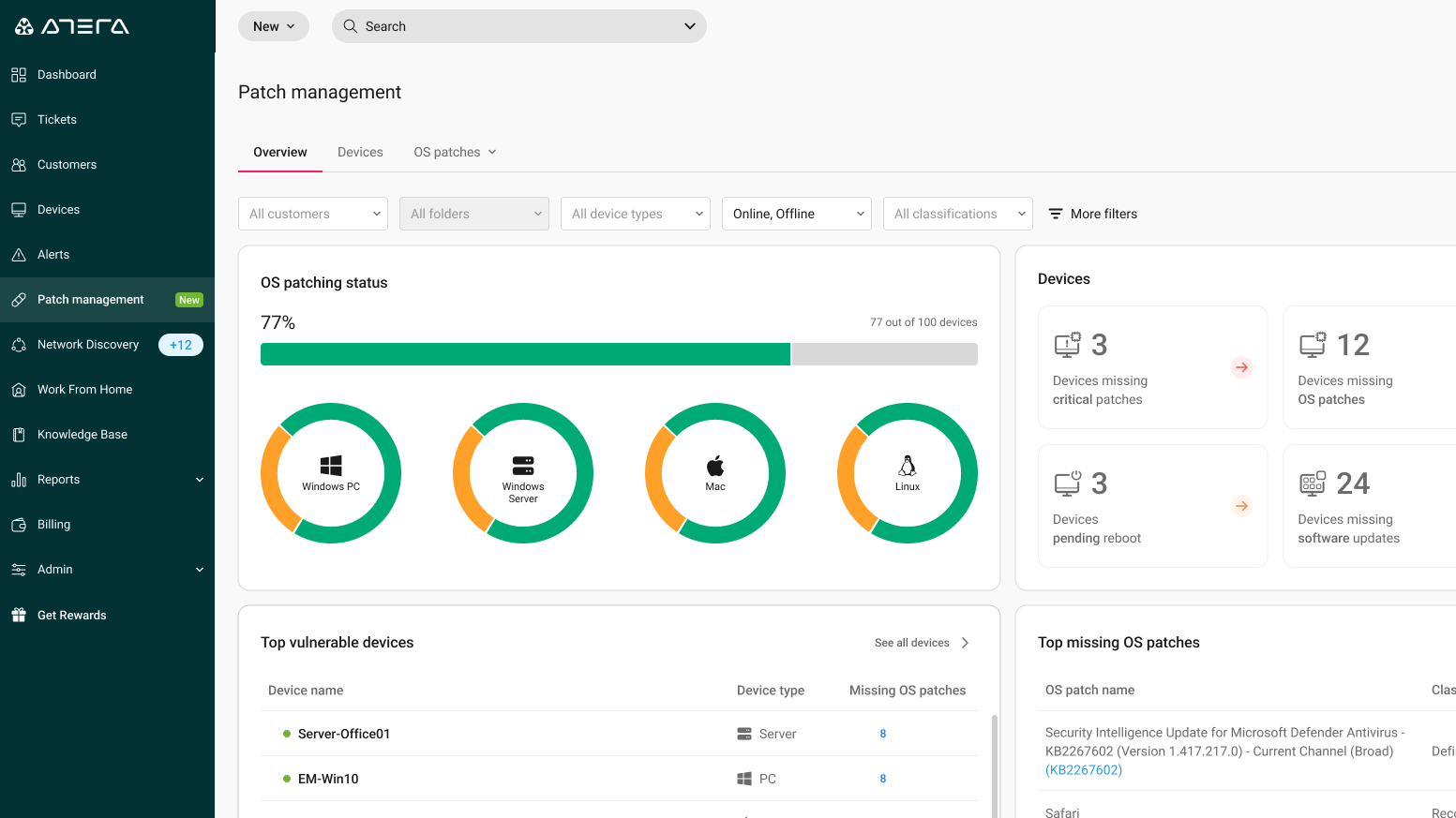
It’s a shift from just using vulnerability management tools to having a system that actually thinks and acts for you.
This new approach enables you to shrink your attack surface by continuously monitoring and resolving issues.
There’s no more waiting for a person to get around to a task.
Atera’s AI automates the entire vulnerability assessment and remediation process.
It keeps you safe by working 24/7, so you can stop playing catch-up.
Benefits of Going Autonomous
You might be thinking, “This sounds great, but what does it really do for me?”
The move from traditional vulnerability management to an autonomous approach has huge benefits.
It’s about more than just finding problems; it’s about solving them and making your whole system safer.
With Atera, you get a true partner that helps your security teams work smarter.
Here’s what you get with continuous vulnerability management:
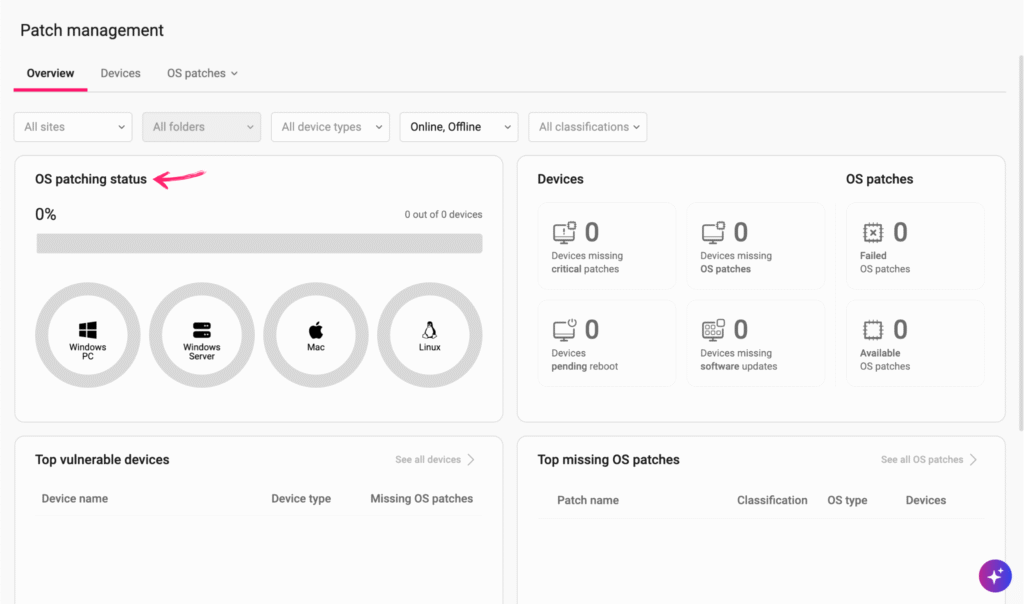
1. Save Time & Money
Traditional vulnerability management is time-consuming.
Your IT staff has to run vulnerability scans and then manually remediating vulnerabilities.
With an autonomous solution, those repetitive jobs are handled for you, freeing up your team to focus on more important tasks.
This also reduces the need to hire more people to keep up.
2. Security Gets a Big Upgrade
Vulnerability management refers to finding and fixing security weaknesses.
Atera’s AI uses real-time threat intelligence to find new vulnerabilities as soon as they appear.
It also knows the difference between a minor issue and a major threat, using risk-based prioritization to focus on the biggest dangers first.
This boosts your overall security posture by proactively stopping attacks.
3. Prioritize What Matters Most
It’s impossible to fix every single issue at once.
The AI in Atera’s system uses a common vulnerability scoring system to help you prioritize vulnerabilities.
This means you can focus on remediating security weaknesses that pose the highest risk to your business, not just the ones that are easiest to fix.
4. Works Everywhere
Whether your systems are in an office or spread across different cloud environments, Atera works the same.
It helps you manage and address vulnerabilities, regardless of their location.
This represents a significant advancement over older management solutions that were limited to working on a local network.
5. Fixes Are Automatic
Instead of creating a long list of problems for your team to solve, Atera’s Loading... solutions handle the work for you.
It automatically applies patches to fix known vulnerabilities, so you don’t have to worry about them anymore.
This ensures that your system is always as secure as possible without manual effort.
Leading the Way in Autonomous IT
The key difference between other vulnerability management products and Atera is that Atera is the only true autonomous solution.
It’s the first to move beyond simple Automatisierung to a new level of intelligent action.
Other remediation tools might help with one part of the job.
Atera’s AI is built to handle the entire vulnerability management process for you.
It’s not just a tool; it’s a new way to work.
Two main AI features power Atera’s platform:
Loading...
IT Autopilot acts as a fully autonomous AI agent.
Its primary function is to handle routine, low-risk IT tasks without human intervention, allowing your team to focus on more complex projects.
It’s the engine behind Atera’s vulnerability management program and its autonomous features.
- 24/7 Support: This AI agent is always on, providing constant support for end-users and systems, which helps to reduce risk significantly and ensures issues are addressed immediately.
- Proactive Problem Solving: IT Autopilot doesn’t wait for a ticket to be submitted. It works proactively to detect vulnerabilities and unaddressed vulnerabilities before they become a major security incident, helping to strengthen your network security.
- Tier-1 Ticket Resolution: The agent can handle and resolve up to 40% of IT workloads by automating common, repetitive tasks like password resets, reboots, and other simple security issues.
- Device and Cloud Support: It can diagnose and fix issues on various it systems, including physical servers, virtual machines, and cloud workloads, providing comprehensive coverage across your organization’s network.

Loading...
AI Copilot is designed to assist human technicians, not replace them.
It acts as a powerful companion that speeds up and simplifies complex tasks, helping your team work smarter and faster.
- Script Generation: AI Copilot can turn simple, plain-text descriptions into powerful scripts in seconds, which is a massive help for remediation efforts.
- Echtzeit-Einblicke: It provides instant context and summaries of tickets and remote sessions. This means your team can skip manually reviewing long histories and get straight to the root cause of the problem.
- Intelligent Search and Filtering: You can use natural language to search for Geräte or assets, for example, “Show me all laptops that haven’t been updated in 30 days,” which makes managing your asset inventory much more efficient.
- Automated Documentation: It can automatically turn resolved support tickets into knowledge base articles, creating a library of solutions that gets smarter with every interaction.

These two features work together to give you a complete, continuous discovery system for your asset inventory.
This helps protect your sensitive Daten from threats that gain unauthorized access.
It lowers your organization’s attack surface and prevents data breaches by tackling security issues in a timely manner.
This is how you build a strong overall security posture.
Atera’s approach is a huge step forward for network security.
It turns a very challenging task into something simple.
It handles everything from web applications to user accounts, ensuring all your assets are protected.
Abschluss
In the past, managing vulnerabilities was a tough job.
You had to do a lot of manual work to find known and potential vulnerabilities in your operating systems and cloud assets.
Every new threat was a new puzzle.
Tools like penetration testing were helpful, but they could only do so much.
The high risk scores and risk factors of an attack made it a constant worry.
But things have changed. Autonomous Vulnerability Management is the future.
It’s a smart way to handle security that takes the hard work off your plate.
Atera is the leader in this space, with the only truly autonomous solution.
It handles everything for you automatically.
Ready to see how Atera can transform your IT?
It can help you move from a manual, reactive approach to a simple, proactive one.
Don’t just manage your security—make it autonomous.
Häufig gestellte Fragen
What is the most crucial step in vulnerability prioritization?
The most crucial step is a thorough risk assessment to determine which vulnerabilities pose the greatest danger. By evaluating asset importance and asset criticality, you can focus on threats that would cause the most damage to your organization.
How does continuous scanning help to detect threats?
Continuous scanning constantly monitors your systems, including your cloud infrastructure, to detect threats and network devices. This ongoing process catches new issues as soon as they appear, so you can address them before they can be exploited.
What is the purpose of remediation tracking?
The purpose of remediation tracking is to confirm that remediation efforts are completed and to ensure the issue is fully resolved. It enables you to effectively manage the entire process, from initial discovery to final fix.
What role does asset discovery play in event management?
Asset discovery is the foundation of good event management. You can’t protect what you don’t know you have. By identifying all of your devices and systems, you can properly monitor for security issues and respond to incidents across your entire network.
What are risk ratings, and why are they important?
Risk ratings are scores or levels given to vulnerabilities to show their severity. They are important because they help you prioritize what needs to be fixed first, allowing you to focus on the highest-risk issues and improve your overall security posture.